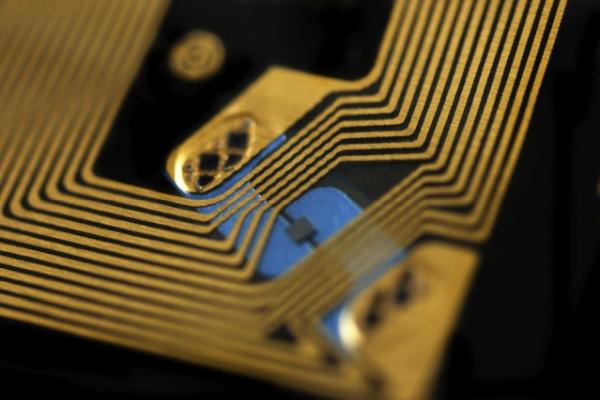
MIT researchers have developed a new type of radio frequency identification (RFID) chip that is extremely difficult to hack.
If such chips were widely adopted, it could mean that an identity thief couldn’t steal your credit card number or key card information by sitting next to you at a café, and high-tech burglars couldn’t swipe expensive goods from a warehouse and replace them with dummy tags.
Texas Instruments has built several prototypes of the new chip, to the researchers’ specifications, and in experiments the chips have behaved as expected. The researchers presented their research this week at the International Solid-State Circuits Conference, in San Francisco.
According to Chiraag Juvekar, a graduate student in electrical engineering at MIT and first author on the new paper, the chip is designed to prevent so-called side-channel attacks. Side-channel attacks analyze patterns of memory access or fluctuations in power usage when a device is performing a cryptographic operation, in order to extract its cryptographic key.
“The idea in a side-channel attack is that a given execution of the cryptographic algorithm only leaks a slight amount of information,” Juvekar says. “So you need to execute the cryptographic algorithm with the same secret many, many times to get enough leakage to extract a complete secret.”
One way to thwart side-channel attacks is to regularly change secret keys. In that case, the RFID chip would run a random-number generator that would spit out a new secret key after each transaction. A central server would run the same generator, and every time an RFID scanner queried the tag, it would relay the results to the server, to see if the current key was valid.
Blackout
Such a system would still, however, be vulnerable to a “power glitch” attack, in which the RFID chip’s power would be repeatedly cut right before it changed its secret key. An attacker could then run the same side-channel attack thousands of times, with the same key. Power-glitch attacks have been used to circumvent limits on the number of incorrect password entries in password-protected devices, but RFID tags are particularly vulnerable to them, since they’re charged by tag readers and have no onboard power supplies.
Two design innovations allow the MIT researchers’ chip to thwart power-glitch attacks: One is an on-chip power supply whose connection to the chip circuitry would be virtually impossible to cut, and the other is a set of “nonvolatile” memory cells that can store whatever data the chip is working on when it begins to lose power.
For both of these features, the researchers — Juvekar; Anantha Chandrakasan, who is Juvekar’s advisor and the Vannevar Bush Professor of Electrical Engineering and Computer Science; Hyung-Min Lee, who was a postdoc in Chandrakasan’s group when the work was done and is now at IBM; and Joyce Kwong, who did her master’s degree and PhD with Chandrakasan and is now at Texas Instruments — use a special type of material known as a ferroelectric crystals.
For more detail: Toward hack-proof RFID chips